AZ 305- Azure Solutions Architect Expert - Topic 02 - Secure Remote Access to Web Applications Using Azure AD Application Proxy and Enterprise Applications
Scenario
Hospitals often face challenges when providing secure remote access to internal applications without VPN access. This article explores how to enable Single Sign-On (SSO) for remote staff accessing an on-premises web application using Azure AD Application Proxy and Azure AD Enterprise Applications.
A hospital has an Azure Active Directory (Azure AD) tenant synced with its on-premises Active Directory. The hospital uses an internal web application called PatientRecordsApp, which is hosted on-premises and uses Integrated Windows Authentication (IWA) for secure access. This app contains sensitive patient data and is critical for doctors and nurses to access patient records.
Challenge
Some doctors work remotely and do not have VPN access to the hospital network. The hospital wants to provide these remote doctors with secure Single Sign-On (SSO) access to PatientRecordsApp without compromising data security or requiring VPN access.
Solution
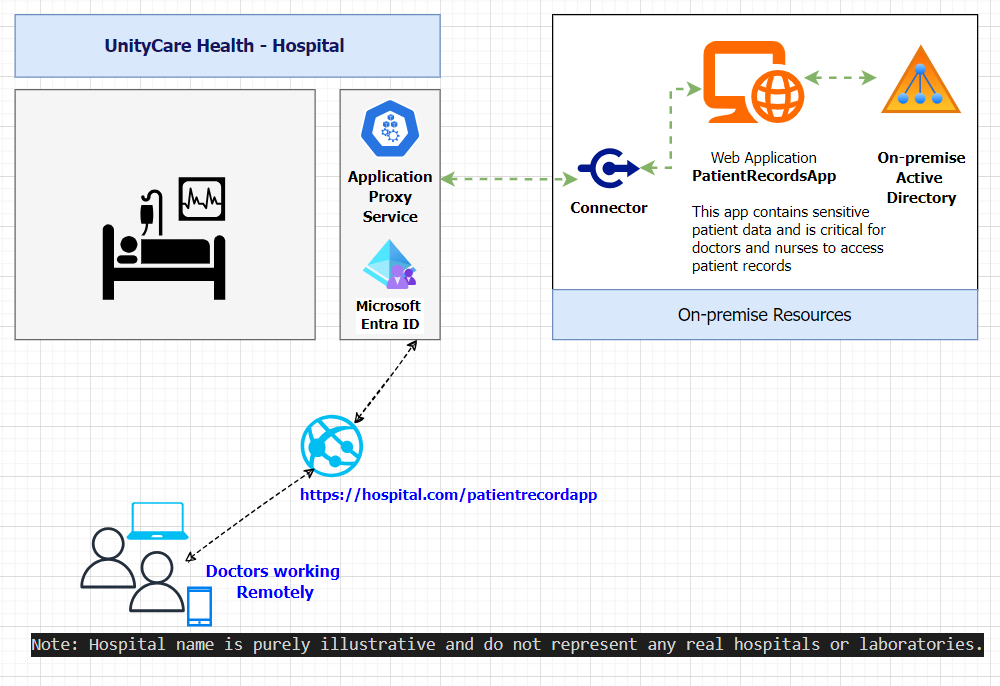
To enable secure SSO access for remote doctors, the hospital should implement:
1 - Azure AD Application Proxy:
- Acts as a secure bridge between Azure AD and the on-premises PatientRecordsApp.
- Allows remote users to securely access on-premises apps without a VPN.
2 - Kerberos Constrained Delegation (KCD):
- Since PatientRecordsApp uses Integrated Windows Authentication, KCD enables Azure AD to authenticate users on behalf of the remote doctors using their synced Active Directory credentials.
How it Works
- A remote doctor accesses the PatientRecordsApp via a secure Azure AD Application Proxy link.
- Azure AD authenticates the doctor using their cloud credentials.
- If successful, the Application Proxy forwards the request to the on-premises PatientRecordsApp server.
- KCD ensures the doctor’s identity is validated and grants access to the app.
Steps
Step 1: Setup Azure AD Application Proxy
-
Install the Application Proxy Connector:
Install the Azure AD Application Proxy Connector on a server inside the hospital’s network. Ensure the server can communicate with both the Azure AD and the on-premises app.
-
Register the Connector:
Sign in to Azure Portal. Go to Azure Active Directory > Application Proxy > Connectors. Verify the Connector status shows as active.
Step 2: Publish the On-Premises Web App
-
Add a New Application
-
Go to Azure AD > Enterprise Applications > New Application > Add an On-Premises Application.
-
Configure Application Proxy Settings:
- Internal URL: http://PatientRecordsApp.local (the internal URL for the web app).
- External URL: https://PatientRecordsApp-hospital.msappproxy.net.
- Pre-authentication: Set to Azure AD for SSO.
- Assign Users & Groups:
- Under Users and Groups, assign the remote doctors and staff who need access.
Step 3: Enable Kerberos Constrained Delegation (KCD)
Since Integrated Windows Authentication (IWA) is used:
-
Enable KCD:
- Go to the on-premises Active Directory.
- Locate the Azure AD Connector machine.
- Set it to allow delegation to the WebApp1 server using Kerberos Constrained Delegation (KCD).
- Map SPN (Service Principal Name):
Ensure the SPN for PatientRecordsApp is correctly registered.
Step 4: Configure Enterprise Application Settings
-
In Azure AD Enterprise Applications:
-
Go to the Enterprise Application created for PatientRecordsApp.
-
SSO Configuration: Verify Integrated Windows Authentication (IWA) is selected with KCD enabled.
-
Conditional Access (Optional for More Security):
-
Implement Conditional Access Policies (e.g., MFA for external access).
-
